The Growing Significance of Insider Threats in E-commerce
Understanding Insider Threats in E-commerce
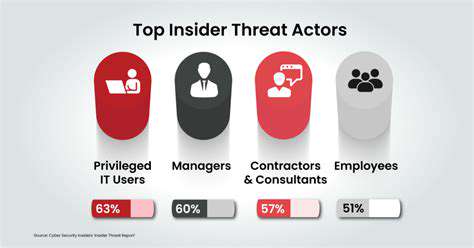
E-commerce platforms are increasingly reliant on internal teams for various operations, from order fulfillment and customer service to data entry and system maintenance. Unfortunately, this reliance also creates a potential vulnerability. Insider threats, encompassing malicious or negligent actions by individuals within the company, can have devastating consequences for e-commerce businesses, ranging from data breaches and financial losses to reputational damage and legal repercussions. Understanding the different types of insider threats is crucial for robust security strategies.
These threats can manifest in numerous ways, from intentionally leaking sensitive customer data to accidentally exposing it through careless practices. Recognizing the subtle indicators and employing proactive measures to mitigate these risks are vital components of a comprehensive security posture.
The Impact of Data Breaches on Customer Trust
A significant concern for any e-commerce platform is the potential for data breaches, often initiated by insider threats. Compromised customer data, including credit card numbers, addresses, and personal information, can result in significant financial losses for customers and damage the company's reputation. The erosion of customer trust following a data breach can be irreparable, leading to a loss of sales and a decline in brand loyalty.
This erosion of trust takes time and effort to rebuild, and it often involves significant financial investment in damage control and recovery efforts. A strong security culture, promoting awareness and vigilance from within, is essential to prevent such incidents.
Financial Losses and Reputational Damage
The financial implications of insider threats extend beyond immediate data breaches. Employees with access to financial systems or sensitive financial data can potentially manipulate transactions, embezzle funds, or engage in fraudulent activities. These actions can lead to substantial financial losses, impacting the company's profitability and long-term viability.
Beyond the immediate financial losses, a breach can significantly damage the company's reputation. Negative publicity and public perception can deter customers and investors, leading to a significant decline in market value and customer confidence. The long-term consequences of such damage can be substantial and lasting.
Employee Negligence and Malicious Intent
Insider threats are not always malicious. Sometimes, simple negligence or a lack of awareness of security protocols can lead to data breaches. Employees might unknowingly click on malicious links, use weak passwords, or fail to properly secure sensitive information, all contributing to vulnerabilities. These inadvertent actions can have severe consequences, especially in the context of e-commerce where sensitive customer data is constantly handled.
The Role of Weak Passwords and Lack of Training
Weak passwords are a common vulnerability exploited by malicious insiders. If employees use easily guessable or reused passwords, it becomes significantly easier for attackers to gain unauthorized access. Lack of proper security training and awareness programs can also contribute to insider threats. Empowering employees with the necessary knowledge and skills to identify and report potential threats is critical in preventing such incidents.
Regular security awareness training can help employees understand the potential risks and how to mitigate them. This education is crucial in fostering a security-conscious culture within the organization.
Implementing Robust Security Measures
E-commerce businesses need to implement robust security measures to address the growing threat of insider attacks. This includes multi-factor authentication, access controls, regular security audits, and strong password policies. Regular security awareness training for all employees is essential to ensure everyone understands the importance of security protocols and potential risks.
Implementing these security measures is crucial not only for preventing data breaches but also for protecting the company's reputation and financial stability. A proactive approach to security is key to mitigating the risks associated with insider threats.
Proactive Security Measures and Employee Monitoring
Proactive security measures go beyond simple policies and procedures. They involve continuous monitoring of employee activity, both online and offline, to identify suspicious patterns. Advanced tools can detect unusual login attempts, suspicious file transfers, or other potentially harmful behaviors. This proactive approach, coupled with a strong security culture, is essential to mitigate the risk of insider threats.
Regular internal audits and security assessments can help identify vulnerabilities and weaknesses in the security system, enabling preventative measures to be put in place. This ongoing vigilance is paramount in the dynamic landscape of e-commerce security.