Security and Trust: Building Confidence in Mobile Transactions
Establishing Trust Through Transparency
Transparency is paramount in building security and trust. Open communication about security procedures, vulnerabilities, and incident responses fosters a sense of reliability with users. Clear, concise documentation outlining these processes is crucial, ensuring users understand the steps taken to protect their data and systems. This transparency builds confidence and encourages user participation in maintaining a secure environment.
Explicitly outlining the security policies and measures used by the organization establishes trust and demonstrates a commitment to data protection. Providing regular updates and progress reports on security initiatives reinforces this commitment and demonstrates the organization's proactive approach to security.
Robust Authentication Mechanisms
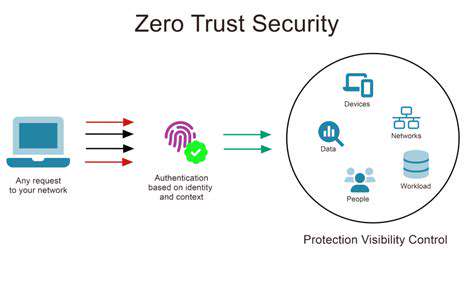
Implementing strong authentication methods is vital for safeguarding sensitive information. Multi-factor authentication (MFA) significantly enhances security by requiring multiple verification steps, making it considerably more difficult for unauthorized users to access accounts. This layered approach dramatically reduces the risk of unauthorized access.
Employing strong password policies and regularly updating them, along with educating users on the importance of secure password management practices, plays a crucial role in bolstering overall security. This proactive approach ensures that passwords are complex and not easily guessable, significantly improving the security posture.
Data Encryption and Protection
Data encryption is essential for protecting sensitive information both in transit and at rest. Using robust encryption algorithms ensures that data is unreadable to unauthorized individuals, even if they gain access to the storage systems or network communications. This protective measure is crucial in maintaining data privacy and confidentiality.
Implementing strong access controls and regular security audits helps detect and rectify vulnerabilities in data protection mechanisms. Regularly evaluating and improving security measures ensures that the organization's defenses are constantly adapting to emerging threats. This proactive approach is critical to maintaining security.
Regular Security Audits and Assessments
Conducting regular security audits and assessments is critical for identifying vulnerabilities and weaknesses in security protocols. These assessments should cover all aspects of the system, including network infrastructure, applications, and data storage. This proactive approach ensures that any potential gaps in security are discovered and addressed before they can be exploited by malicious actors.
Regular security assessments help in identifying and addressing vulnerabilities in a timely manner. Proactive measures like penetration testing and vulnerability scanning are vital to maintaining a secure environment. This proactive approach helps identify and mitigate potential threats.
Incident Response Plan
Developing and testing a comprehensive incident response plan is crucial for handling security breaches and other incidents effectively. This plan should outline procedures for detecting, containing, responding to, and recovering from incidents. A well-defined response plan ensures that the organization can effectively manage and mitigate the impact of security incidents.
Employee Training and Awareness
Providing comprehensive security training and awareness programs to employees is essential for fostering a culture of security. This training should cover topics such as password management, phishing awareness, and safe handling of sensitive data. Equipping employees with the necessary knowledge and skills to recognize and avoid security threats is essential for the overall security posture of the organization.
Regular training reinforces the importance of security protocols and promotes a culture of vigilance among employees. This proactive measure is vital for maintaining security and reducing the risk of human error.